ADVANCING YOUR CYBERSECURIT
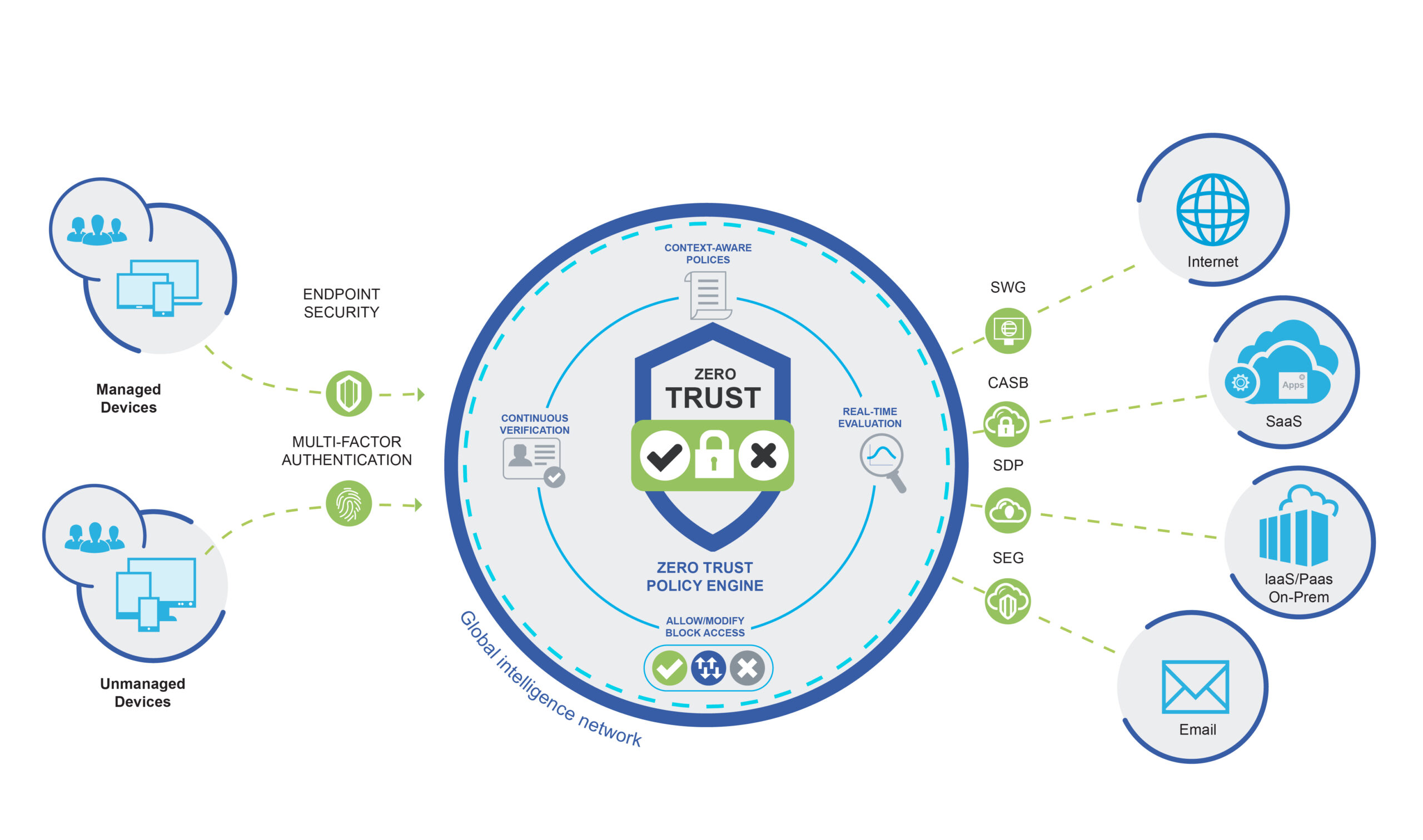
Establish trust, enforce trust-based access, continually verify trust, and respond to change in trust
Embarking on the Zero Trust journey involves a carefully curated collection of integrated security activities. At our core, we combine scale, expertise, technology partnerships, and seamless system integration. This convergence not only streamlines complexities but also ignites a rapid pace of innovation, ensuring your organization stays ahead in today's dynamic cybersecurity landscape.

INTEGRATED END-TO-END APPROACH
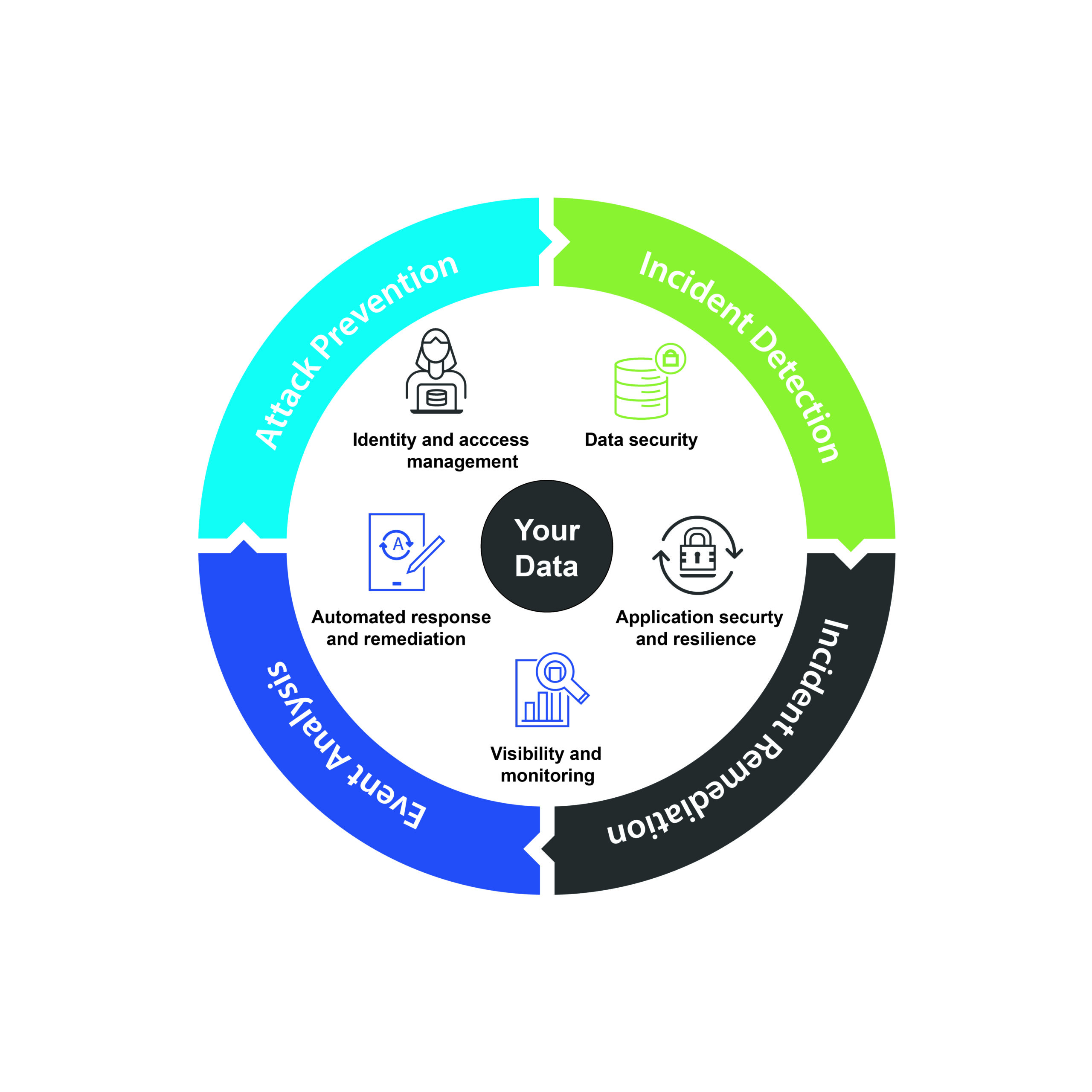
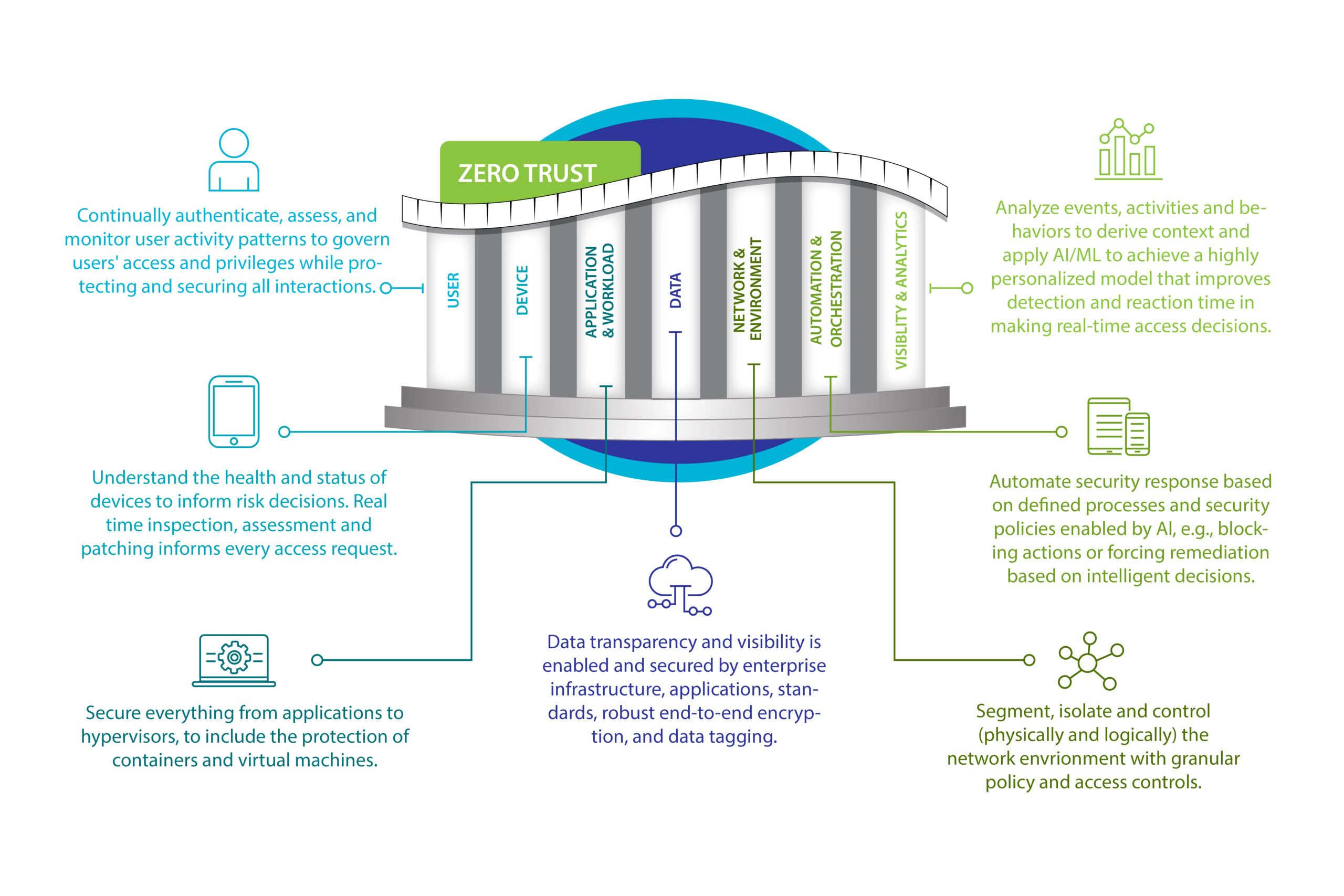
A holistic end-to-end portfolio: user, network, and access
In the realm of Zero Trust security strategy, a comprehensive approach is paramount, encompassing every facet of the organization—from users and devices to applications and data. Zero Trust principles aren’t merely a patchwork solution; they demand seamless integration across all elements for maximum effectiveness. Opting for disjointed point solutions deviates from this strategic imperative.
Enter our robust portfolio, meticulously crafted to provide all the essential Zero Trust solutions for today’s modern organization. By entrusting a single vendor to deliver all necessary technologies, organizations can shed the burden of managing multiple security products. This consolidation leads to cost savings and heightened operational efficiencies, empowering businesses to navigate the evolving cybersecurity landscape with confidence and agility.
MAKE IT WORK
What are the challenges of a Zero Trust Architecture?
Working with Legacy systems
Legacy systems have limited capability when it comes to supporting modern authentication and verification methods. They can also pose network access risks through limited protocol support.

Continuous user and device authentication
Most of the agencies struggle with the ability to continuously authenticate users and devices on ongoing basis and are struggling to monitor users post-authentication. The challenge here is both on the side of the authentication systems and applications.
Scale of deployment can be complex and daunting
The solution is through the right prioritization. When working on ZTA, agencies have to identify the critical users, applications and data that needs to be protected to begin with. In this case, guidelines issued by NIST, CISA, OMB (M-22-09) and DoD's reference also prove very helpful. We have to start with the critical access systems and build outwards.

Change of mindset
Setting up a ZTA and building a ZTA roadmap require a major change in mindset. Especially for a federal agencies, with multiple OpDivs there is a need to build a collaborative approach. ZTA requires that security is viewed as a part of each and every step of IT across data classification, network segmentation, application modernization and user/device authentication.

Impact on App performance & user experience
By enforcing continuous authentication, it can potentially impact app performance. Similarly, the extra security measures such as MFA and continuous authentication can add friction to the user experience. There is a fine balance that needs to be established between security and usability.

Working with Legacy systems
Legacy systems have limited capability when it comes to supporting modern authentication and verification methods. They can also pose network access risks through limited protocol support.

Continuous user and device authentication
Most of the agencies struggle with the ability to continuously authenticate users and devices on ongoing basis and are struggling to monitor users post-authentication. The challenge here is both on the side of the authentication systems and applications.

Scale of deployment can be complex and daunting
The solution is through the right prioritization. When working on ZTA, agencies have to identify the critical users, applications and data that needs to be protected to begin with. In this case, guidelines issued by NIST, CISA, OMB (M-22-09) and DoD's reference also prove very helpful. We have to start with the critical access systems and build outwards.

Change of mindset
Setting up a ZTA and building a ZTA roadmap require a major change in mindset. Especially for a federal agencies, with multiple OpDivs there is a need to build a collaborative approach. ZTA requires that security is viewed as a part of each and every step of IT across data classification, network segmentation, application modernization and user/device authentication.

Impact on App performance & user experience
By enforcing continuous authentication, it can potentially impact app performance. Similarly, the extra security measures such as MFA and continuous authentication can add friction to the user experience. There is a fine balance that needs to be established between security and usability.
SURVIVE AND THRIVE
How to Implement Zero Trust
Embarking on a Zero Trust journey is not merely a choice; it's critical for the survival and growth of today's organizations. To navigate this journey successfully, three pivotal elements must be embraced:
- Knowledge and Conviction: Understanding the transformative potential of modern technology is key. By recognizing how technology can streamline operations, cut costs, and propel organizational objectives forward, you lay the foundation for a robust zero trust framework.
- Disruptive Technologies: Legacy solutions are no longer sufficient in the face of evolving internet threats and dynamic workforces. Embracing disruptive technologies is essential for staying ahead of the curve and fortifying your security posture.
- Cultural and Mindset Change: Cultivating a culture that champions zero trust is paramount. When your teams grasp the advantages it offers, they become advocates, actively driving its adoption and success.
While change may provoke discomfort, particularly when entrenched systems are involved, it’s a hurdle that can be overcome. Breaking the Zero Trust journey into manageable phases is a strategic approach. This is precisely why we advocate a four-step process:
Empower and Secure Your Workforce
Protect Your Data in Cloud Workloads
Modernize Your IoT/OT Security
Engage Your Customers and Suppliers Securely
You gradually transform your network and security infrastructure by methodically advancing through these stages. Ultimately, you achieve a Zero Trust architecture that securely interconnects users, devices, and applications across any network, regardless of their location. This proactive approach mitigates risks and fosters agility and resilience in the face of an ever-evolving threat landscape.
what can we do
Framework and the iCallidus Differentiator
Collaborate with iCallidus to guide you through building a Zero Trust Security Framework. We will work with your team and help answer some of the key questions like
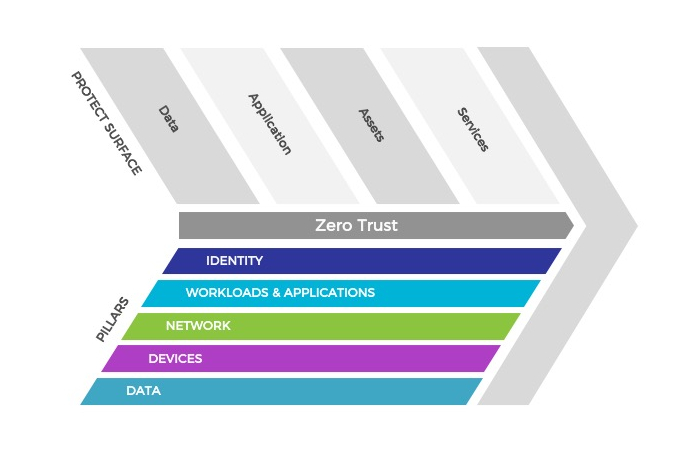
How to build a Zero Trust driven cybersecurity program
Which ZT pillar(s) should your agency start with, depending on your current state of cybersecurity policies and practices
What are the key challenges to watch out for while building and executing a Zero Trust program
Is my agency compliant with FY-24 Zero Trust goals as laid out in OMB M-22-09
What level of co-ordination is required across various OpDivs to manage a Zero Trust framework
WE CAN HELP
Unlock the power of Zero
Trust Security
Partner with iCallidus to develop a tailored Zero Trust Security
Framework for your organization. Together, we’ll address critical questions:
→ How can a Zero Trust cybersecurity program be constructed to bolster
defenses against evolving threats?
→ Which Zero Trust pillars should your organization prioritize based on
current cybersecurity policies?
→ Is your organization aligned with FY-24 Zero Trust objectives for
compliance and readiness?
→ What coordination is needed across Operational Divisions to effectively
manage a Zero Trust framework?
→ How do we mitigate key challenges during development and
implementation?
Trust principles. Let’s navigate complexities and pave the way for a resilient
cybersecurity landscape. Contact us at zerotrust@icallidus.com
Capabilities
Human-Centered Design (HCD)
Zero Trust Security
IT Transformation & Architecture
Application Modernization
DevSecOps
Program Management Office (PMO)
Contact us
info@icallidus.com
10630 Little Patuxent
Pkwy
Suite 405
Columbia, MD 21044
© 2024 ICallidus All Rights Reserved